Fortinet NSE4_FGT-7.0 Real Dumps, Real NSE4_FGT-7.0 Questions To Share Without Taking RisksFortinet NSE4_FGT-7.0 Real Dumps, Real NSE4_FGT-7.0 Questions To Share Without Taking Risks

Although life is an adventure, for the Fortinet NSE4_FGT-7.0 exam, I am afraid that no one is willing to take a risk. How did the Fortinet NSE4_FGT-7.0 exam pass without risk? This is what many test-takers want to ask. Pass4itSure Fortinet NSE4_FGT-7.0 dumps provide test takers with targeted training and high-quality practice, and the real question dumps are very similar to the real question exam to ensure that you pass smoothly.
Choose it, you don’t have to take risks! real NSE4_FGT-7.0 dumps (PDF +VCE) https://www.pass4itsure.com/nse4_fgt-7-0.html Free choice of two modes, happy learning.
Pass NSE4_FGT-7.0 with Fortinet NSE4_FGT-7.0 real dumps
Fortinet NSE 4 – FortiOS 7.0 – Exam series: NSE4_FGT-7.0. The number of questions: 60. Exam time: 105 minutes. Language: English and Japanese. Product version: FortiOS 7.0
Pass4itSure NSE4_FGT-7.0 dumps provide high-quality practice quizzes around real exam content in two formats (PDF and VCE) and are the best preparation for taking Fortinet NSE4_FGT-7.0 certification.
Pass4itSure NSE4_FGT-7.0 real dumps pdf, real NSE4_FGT-7.0 questions
Participate in free exercises to improve your exam skills, answers are at the end of the questions.
[1]
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
A. The subject field in the server certificate
B. The serial number in the server certificate
C. The server name indication (SNI) extension in the client hello message
D. The subject alternative name (SAN) field in the server certificate
E. The host field in the HTTP header
Reference: https://checkthefirewall.com/blogs/fortinet/ssl-inspection
[2]
When configuring a firewall virtual wire pair policy, which the following statement is true?
A. Any number of virtual wire pairs can be included, as long as the policy traffic direction is the same.
B. Only a single virtual wire pair can be included in each policy.
C. Any number of virtual wire pairs can be included in each policy, regardless of the policy traffic direction settings.
D. Exactly two virtual wire pairs need to be included in each policy.
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD48690
[3]
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
A. The interface has been configured for a one-arm sniffer.
B. The interface is a member of a virtual wire pair.
C. The operation mode is transparent.
D. The interface is a member of a zone.
E. Captive portal is enabled in the interface.
[4]
Refer to the exhibit.
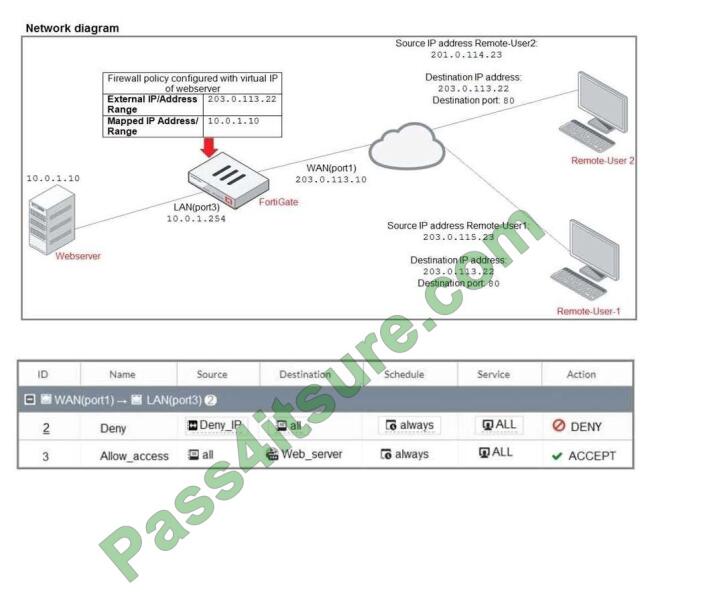
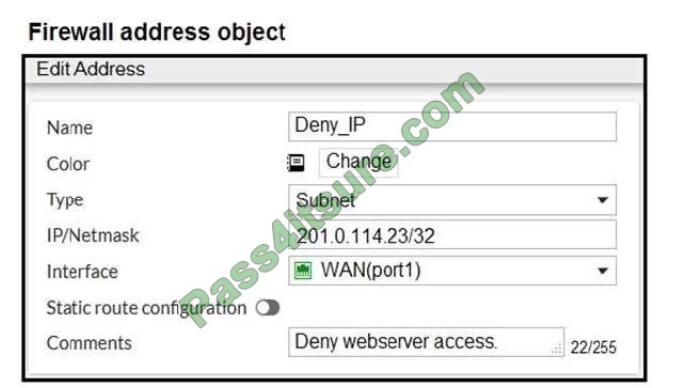
The exhibit contains a network diagram, firewall policies, and a firewall address object configuration. An
administrator created a Deny policy with default settings to deny Webserver access for Remote- user2.
Remote-user2 is still able to access Webserver.
Which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose
two.)
A. Disable match-VIP in the Deny policy.
B. Set the Destination address as Deny_IP in the Allow-access policy.
C. Enable match VIP in the Deny policy.
D. Set the Destination address as Web_server in the Deny policy.
[5]
Which certificate value can FortiGate use to determine the relationship between the issuer and the certificate?
A. Subject Key Identifier value
B. SMMIE Capabilities value
C. Subject value
D. Subject Alternative Name value
[6]
Examine this PAC file configuration.
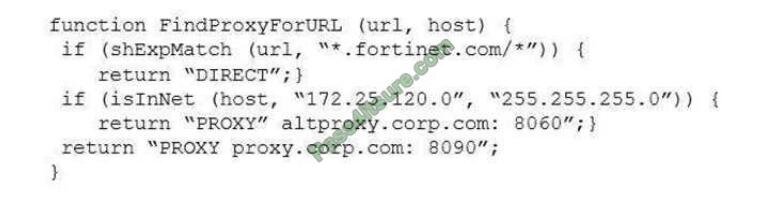
Which of the following statements are true? (Choose two.)
A. Browsers can be configured to retrieve this PAC file from the FortiGate.
B. Any web request to the 172.25.120.0/24 subnet is allowed to bypass the proxy.
C. All requests not made to Fortinet.com or the 172.25.120.0/24 subnet, have to go through altproxy.corp.com: 8060.
D. Any web request fortinet.com is allowed to bypass the proxy.
[7]
Which two statements about antivirus scanning mode are true? (Choose two.)
A. In proxy-based inspection mode, files bigger than the buffer size are scanned.
B. In flow-based inspection mode. FortiGate buffers the file, but also simultaneously transmits it to the client.
C. In proxy-based inspection mode, antivirus scanning buffers the whole file for scanning, before sending it to the client.
D. In flow-based inspection mode, files bigger than the buffer size is scanned.
[8]
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
A. It limits the scope of application control to the browser-based technology category only.
B. It limits the scope of application control to scan application traffic based on application category only.
C. It limits the scope of application control to scan application traffic using parent signatures only
D. It limits the scope of application control to scan application traffic on DNS protocol only.
[9]
If Internet Service is already selected as Source in a firewall policy, which other configuration objects can be added to the Source field of a firewall policy?
A. IP address
B. Once Internet Service is selected, no other object can be added
C. User or User Group
D. FQDN address
Reference: https://docs.fortinet.com/document/fortigate/6.2.5/cookbook/179236/using-internet-service-inpolicy
[10]
Which of the following statements about central NAT are true? (Choose two.)
A. IP tool references must be removed from existing firewall policies before enabling central NAT.
B. Central NAT can be enabled or disabled from the CLI only.
C. Source NAT, using central NAT, requires at least one central SNAT policy.
D. Destination NAT, using central NAT, requires a VIP object as the destination address in a firewall.
[11]
View the exhibit.
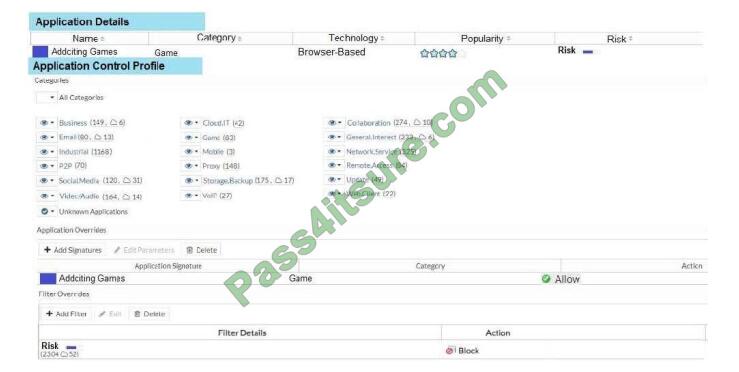
A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting Games). Based on this configuration, which statement is true?
A. Addicting. Games are allowed based on the Application Overrides configuration.
B. Addicting. Games are blocked on the Filter Overrides configuration.
C. Addicting. Games can be allowed only if the Filter Overrides actions are set to Exempt.
D. Addicting. Games are allowed based on the Categories configuration.
[12]
An administrator wants to configure timeouts for users. Regardless of the user\\’s behavior, the timer should start as soon as the user authenticates and expire after the configured value.
Which timeout option should be configured on FortiGate?
A. auth-on-demand
B. soft-timeout
C. idle-timeout
D. new-session
E. hard-timeout
Correct answer posted
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| BDE | A | ABC | AB | C | AD | CD | B | A | AB | A | E |
Here is part of the free latest NSE4_FGT-7.0 PDF exam questions from Google Drive:
free latest NSE4_FGT-7.0 exam pdf https://drive.google.com/file/d/1sy_OhICkSefBD3xmOAzzgRJVLiDOduot/view?usp=sharing
More Fortinet certification popular exam practices
https://www.cert4sure.net/new-fortinet-nse7_ots-6-4-dumps-to-start-your-exam-planning.html
https://www.cert4sure.net/fortinet-nse7_efw-6-4-dumps-pdf-latest-exam-practice-test-questions.html
https://www.cert4sure.net/most-effective-success-fortinet-nse4_fgt-6-4-dumps-pdf-problem.html
The success that NSE4_FGT-7.0 dumps brings to every test taker is real. No more taking risks. Dreams and hopes are important but more important are to practice and prove. To pass the exam successfully, you also need to practice the NSE4_FGT-7.0 exam questions a lot.
Full NSE4_FGT-7.0 dumps https://www.pass4itsure.com/nse4_fgt-7-0.html (166 total issues)
Happy to share useful NSE4_FGT-7.0 learning materials. good luck! !!