Free exam study guide for the new CompTIA CS0-002 (+ useful CS0-002 dumps download)Free exam study guide for the new CompTIA CS0-002 (+ useful CS0-002 dumps download)
Cert4sure’s CompTIA CS0-002 exam study guide fully follows the full set of exam topics of the new CySA + CS0-002 exam. Due to the lack of learning resources for the CS0-002 exam, we have compiled and shared CS0-002 learning materials that are beneficial to all of us, including the Latest CS0-002 practice questions, latest CS0-002 pdf dumps, Recommended websites https://www.pass4itsure.com/cs0-002.html and purchase discount codes.
CompTIA CS0-002 Exam Study Guide: https://drive.google.com/file/d/19rf_Cc80SIO3i1YsM541KiFZEtDj8zyT/view?usp=sharing
Candidates preparing to take the CYSA+ (CS0-001) exam should not worry, because the English version will be retired on October 21, 2020, while the simple Chinese and Japanese versions will be retired on April 23, 2021.

Q&As: About the Pass4itsure CompTIA CySA+ CS0-002 exam dumps
- How many questions in the real CS0-002 exam?
There are 119 Q&As in our CompTIA CS0-002 real exam questions. - Can I get the updated version of CS0-002 real exam questions?
Yes, from the date of your purchasing, you can get a FREE update of CompTIA CS0-002 real exam questions in ONE year. - Can I get a full refund if I fail the CS0-002 exam?
Yes, if you fail the CS0-002 exam by using our CompTIA CompTIA CySA+ real exam questions, you can get a full refund. - Can I get a big discount if I buy many exams?
The latest discount code “2020PASS” is provided below. Get 12% off!
CompTIA CS0-002 PDF download
[free pdf] CompTIA CS0-002 pdf dumps https://drive.google.com/file/d/19rf_Cc80SIO3i1YsM541KiFZEtDj8zyT/view?usp=sharing
Practice CS0-002 real questions: CompTIA Cybersecurity Analyst (CySA+)
QUESTION 1
A compliance officer of a large organization has reviewed the firm\\’s vendor management program but has discovered
there are no controls defined to evaluate third-party risk or hardware source authenticity. The compliance officer wants
to gain some level of assurance on a recurring basis regarding the implementation of controls by third parties.
Which of the following would BEST satisfy the objectives defined by the compliance officer? (Choose two.)
A. Executing vendor compliance assessments against the organization\\’s security controls
B. Executing NDAs prior to sharing critical data with third parties
C. Soliciting third-party audit reports on an annual basis
D. Maintaining and reviewing the organizational risk assessment on a quarterly basis
E. Completing a business impact assessment for all critical service providers
F. Utilizing DLP capabilities at both the endpoint and perimeter levels
Correct Answer: AE
QUESTION 2
An information security analyst observes anomalous behavior on the SCADA devices in a power plant. This behavior
results in the industrial generators overheating and destabilizing the power supply. Which of the following would BEST
identify potential indicators of compromise?
A. Use Burp Suite to capture packets to the SCADA device\\’s IP.
B. Use tcpdump to capture packets from the SCADA device IP.
C. Use Wireshark to capture packets between SCADA devices and the management system.
D. Use Nmap to capture packets from the management system to the SCADA devices.
Correct Answer: C
QUESTION 3
A development team uses open-source software and follows an Agile methodology with two-week sprints. Last month,
the security team filed a bug for an insecure version of a common library. The DevOps team updated the library on the
server, and then the security team rescanned the server to verify it was no longer vulnerable. This month, the security
team found the same vulnerability on the server.
Which of the following should be done to correct the cause of the vulnerability?
A. Deploy a WAF in front of the application.
B. Implement a software repository management tool.
C. Install a HIPS on the server.
D. Instruct the developers to use input validation in the code.
Correct Answer: B
QUESTION 4
An audit has revealed an organization is utilizing a large number of servers that are running unsupported operating
systems.
As part of the management response phase of the audit, which of the following would BEST demonstrate senior
management is appropriately aware of and addressing the issue?
A. Copies of prior audits that did not identify the servers as an issue
B. Project plans relating to the replacement of the servers that were approved by management
C. Minutes from meetings in which risk assessment activities addressing the servers were discussed
D. ACLs from perimeter firewalls showing blocked access to the servers
E. Copies of change orders relating to the vulnerable servers
Correct Answer: C
QUESTION 5
A product manager is working with an analyst to design a new application that will perform as a data analytics platform
and will be accessible via a web browser. The product manager suggests using a PaaS provider to host the application.
Which of the following is a security concern when using a PaaS solution?
A. The use of infrastructure-as-code capabilities leads to an increased attack surface.
B. Patching the underlying application server becomes the responsibility of the client.
C. The application is unable to use encryption at the database level.
D. Insecure application programming interfaces can lead to data compromise.
Correct Answer: B
QUESTION 6
A small electronics company decides to use a contractor to assist with the development of a new FPGA-based device.
Several of the development phases will occur off-site at the contractor\\’s labs. Which of the following is the main
concern a security analyst should have with this arrangement?
A. Making multiple trips between development sites increases the chance of physical damage to the FPGAs.
B. Moving the FPGAs between development sites will lessen the time that is available for security testing.
C. Development phases occurring at multiple sites may produce change management issues.
D. FPGA applications are easily cloned, increasing the possibility of intellectual property theft.
Correct Answer: D
Reference: https://www.eetimes.com/how-to-protect-intellectual-property-in-fpgas-devices-part-1/#
QUESTION 7
A Chief Information Security Officer (CISO) is concerned the development team, which consists of contractors, has too
much access to customer data. Developers use personal workstations, giving the company little to no visibility into the
development activities.
Which of the following would be BEST to implement to alleviate the CISO\\’s concern?
A. DLP
B. Encryption
C. Test data
D. NDA
Correct Answer: A
QUESTION 8
Bootloader malware was recently discovered on several company workstations. All the workstations run Windows and
are current models with UEFI capability. Which of the following UEFI settings is the MOST likely cause of the
infections?
A. Compatibility mode
B. Secure boot mode
C. Native mode
D. Fast boot mode
Correct Answer: A
QUESTION 9
A security analyst is reviewing packet captures from a system that was compromised. The system was already isolated
from the network, but it did have network access for a few hours after being compromised. When viewing the capture in
a packet analyzer, the analyst sees the following:

Which of the following can the analyst conclude?
A. Malware is attempting to beacon to 128.50.100.3.
B. The system is running a DoS attack against ajgidwle.com.
C. The system is scanning ajgidwle.com for PII.
D. Data is being exfiltrated over DNS.
Correct Answer: C
QUESTION 10
A security analyst is reviewing vulnerability scan results and notices new workstations are being flagged as having
outdated antivirus signatures. The analyst observes the following plugin output:
Antivirus is installed on the remote host:
Installation path: C:\Program Files\AVProduct\Win32\
Product Engine: 14.12.101
Engine Version: 3.5.71
Scanner does not currently have information about AVProduct version 3.5.71. It may no longer be supported.
The engine version is out of date. The oldest supported version from the vendor is 4.2.11.
The analyst uses the vendor\\’s website to confirm the oldest supported version is correct.
Which of the following BEST describes the situation?
A. This is a false positive, and the scanning plugin needs to be updated by the vendor.
B. This is a true negative, and the new computers have the correct version of the software.
C. This is a true positive, and the new computers were imaged with an old version of the software.
D. This is a false negative, and the new computers need to be updated by the desktop team.
Correct Answer: D
QUESTION 11
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set
up each of the tools according to the respective vendor\\’s instructions and generated a report of vulnerabilities that ran
against the same target server.
Tool A reported the following:
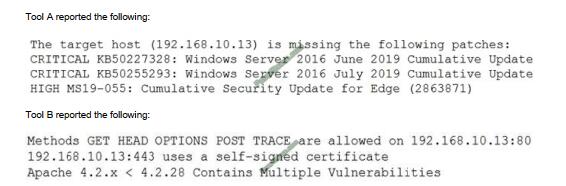
Which of the following BEST describes the method used by each tool? (Choose two.)
A. Tool A is agent based.
B. Tool A used fuzzing logic to test vulnerabilities.
C. Tool A is unauthenticated.
D. Tool B utilized machine learning technology.
E. Tool B is agent based.
F. Tool B is unauthenticated.
Correct Answer: CE
QUESTION 12
A security technician is testing a solution that will prevent outside entities from spoofing the company\\’s email domain,
which is comptia.org. The testing is successful, and the security technician is prepared to fully implement the solution.
Which of the following actions should the technician take to accomplish this task?
A. Add TXT @ “v=spf1 mx include:_spf.comptia.org -all” to the DNS record.
B. Add TXT @ “v=spf1 mx include:_spf.comptia.org -all” to the email server.
C. Add TXT @ “v=spf1 mx include:_spf.comptia.org +all” to the domain controller.
D. Add TXT @ “v=spf1 mx include:_spf.comptia.org +all” to the web server.
Correct Answer: A
Reference: https://blog.finjan.com/email-spoofing
QUESTION 13
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL:
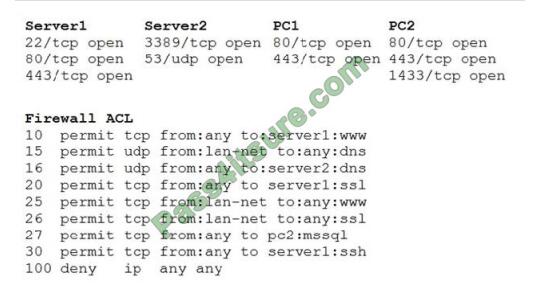
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current
functionality?
A. PC1
B. PC2
C. Server1
D. Server2
E. Firewall
Correct Answer: E
CompTIA CS0-002 exam video
Pass4itsure has the following characteristics:

What customers say about Pass4itsure
Pass4itsure discount code 2020
Please read the picture carefully to get 12% off!

Conclusion:
2020 Pass4itsure CompTIA CS0-002 Exam Dumps (PDF ) Free Share: https://drive.google.com/file/d/19rf_Cc80SIO3i1YsM541KiFZEtDj8zyT/view?usp=sharing
2020 Pass4itsure CompTIA Full Series Exam Dumps (PDF ) Free Share: https://www.exampass.net/?s=CompTIA
The new CompTIA CYSA+ (CS0-002) certification exam will take effect on April 21, 2020. This study guide shares the learning materials for the new exam CS0-002. Recommended websites https://www.pass4itsure.com/cs0-002.html CS0-002 dumps Q&As.