NSE4_FGT-7.0 Dumps Updated Valid Fortinet NSE 4 – FortiOS 7.0 Preparation MaterialNSE4_FGT-7.0 Dumps Updated Valid Fortinet NSE 4 – FortiOS 7.0 Preparation Material
Effective preparation for the Fortinet NSE 4 – FortiOS 7.0 exam will do more with less. Test takers choose a valid Fortinet NSE 4 – FortiOS 7.0 preparation material to prepare for the NSE4_FGT-7.0 exam to advance their careers. We have updated the valid NSE4_FGT-7.0 dumps to help you prepare for the exam.
Our NSE4_FGT-7.0 dumps page: https://www.pass4itsure.com/nse4_fgt-7-0.html has NSE4_FGT-7.0 PDFs and software to help you thoroughly learn all the questions and answers.
Passing the NSE4_FGT-7.0 exam requires selecting appropriate study materials to prepare for the exam.
NSE4_FGT-7.0 Fortinet exam do you have to pass?
The Fortinet NSE 4—FortiOS 7.0 exam is part of the NSE 4 Cybersecurity Professional Program and recognizes successful candidates’ knowledge and expertise in FortiGate. If you want to be certified, you must pass successfully.
What should I pay attention to for the Fortinet NSE 4 – FortiOS 7.0 exam?
Exam name: Fortinet NSE 4—FortiOS 7.0
Exam series: NSE4_FGT-7.0
Time allowed: 105 minutes
Exam questions: 60 multiple-choice questions
Language: English and Japanese
Product version: FortiOS 7.0
Official resources:
NSE 4 FortiGate Security 7.0
NSE 4 FortiGate Infrastructure 7.0
FortiOS 7.0—Administration Guide
FortiOS 7.0—New Features Guide
Prepare resources efficiently: Pass4itSure NSE4_FGT-7.0 Dumps
The above is some basic knowledge about Fortinet NSE 4 – FortiOS 7.0 exam, you must know, then you need to find good preparation materials to practice.
Where can I get NSE4_FGT-7.0 dumps to prepare for the exam?
Pass4itSure NSE4_FGT-7.0 dumps are the right choice for you. The current NSE4_FGT-7.0 dumps in Pass4itSure are real, which can be the key to easily passing the Fortinet NSE 4 – FortiOS 7.0 exam.
Free NSE4_FGT-7.0 exam questions answers
QUESTION # 1
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for example.com home page, the override must be configured using a specific syntax. Which two syntaxes are correct to configure web rating for the home page? (Choose two.)
A. www.example.com:443
B. www.example.com
C. example.com
D. www.example.com/index.html
Correct Answer: BD
QUESTION # 2
Which two statements about IPsec authentication on FortiGate are correct? (Choose two.)
A. For a stronger authentication, you can also enable extended authentication (XAuth) to request the remote peer to provide a username and password
B. FortiGate supports pre-shared key and signature as authentication methods.
C. Enabling XAuth results in faster authentication because fewer packets are exchanged.
D. A certificate is not required on the remote peer when you set the signature as the authentication method.
Correct Answer: BD
QUESTION # 3
Refer to the exhibit.
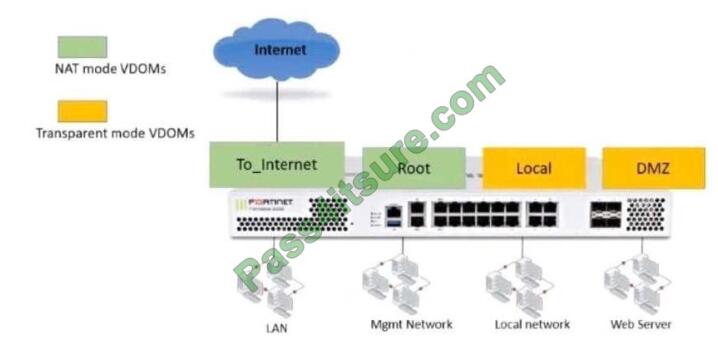
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are
configured in transparent mode. The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the internet.
The To_lnternet VDOM is the only VDOM with internet access and is directly connected to the ISP modem.
Which two statements are true? (Choose two.)
A. Inter-VDOM links are required to allow traffic between the Local and Root VDOMs.
B. A static route is required on the To_Internet VDOM to allow LAN users to access the internet.
C. Inter-VDOM links are required to allow traffic between the Local and DMZ VDOMs.
D. Inter-VDOM links are not required between the Root and To_Internet VDOMs because the Root VDOM is used only as a management VDOM.
Correct Answer: AD
QUESTION # 4
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
A. The firmware image must be manually uploaded to each FortiGate.
B. Only secondary FortiGate devices are rebooted.
C. Uninterruptable upgrade is enabled by default.
D. Traffic load balancing is temporally disabled while upgrading the firmware.
Correct Answer: CD
QUESTION # 5
A FortiGate is operating in NAT mode and configured with two virtual LAN (VLAN) sub-interfaces added to the physical interface. Which statements about the VLAN sub-interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
A. The two VLAN sub-interfaces can have the same VLAN ID, only if they have IP addresses in different subnets.
B. The two VLAN sub-interfaces must have different VLAN IDs.
C. The two VLAN sub-interfaces can have the same VLAN ID, only if they belong to different VDOMs.
D. The two VLAN sub-interfaces can have the same VLAN ID, only if they have IP addresses in the same subnet.
Correct Answer: B
FortiGate_Infrastructure_6.0_Study_Guide_v2-Online.pdf ?gt; page 147 “Multiple VLANs can coexist in the same physical interface, provide they have different VLAN ID”
QUESTION # 6
By default, FortiGate is configured to use HTTPS when performing live web filtering with FortiGuard
servers. Which two CLI commands will cause FortiGate to use an unreliable protocol to communicate with
FortiGuard servers for live web filtering? (Choose two.)
A. set fortiguard anycast disable
B. set protocol UDP
C. set web filter-force-off to disable
D. set web filter-cache to disable
Correct Answer: AC
QUESTION # 7
Refer to the exhibit, which contains a radius server configuration.
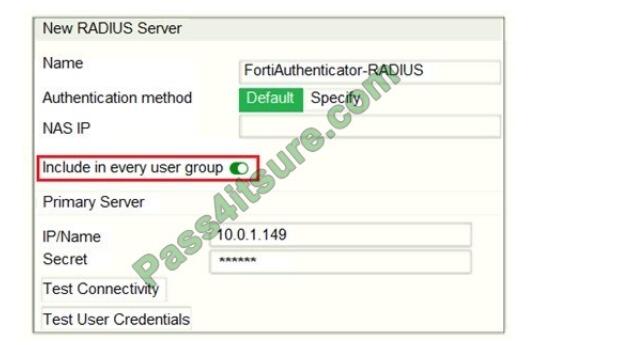
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option. What will be the impact of using Include in every user group option in a RADIUS configuration?
A. This option places the RADIUS server and all users who can authenticate against that server, into every FortiGate user group.
B. This option places all FortiGate users and groups required to authenticate into the RADIUS server, which, in this case, is FortiAuthenticator.
C. This option places all users into every RADIUS user group, including groups that are used for the LDAP server on FortiGate.
D. This option places the RADIUS server, and all users who can authenticate against that server, into every RADIUS group.
Correct Answer: A
QUESTION # 8
Refer to the exhibit.
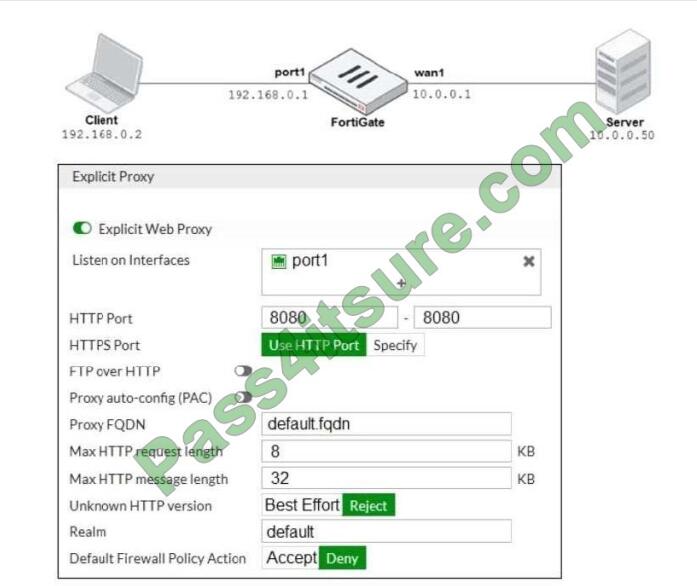
The exhibits show a network diagram and the explicit web proxy configuration. In the command diagnose sniffer packet, what filter can you use to capture the traffic between the client and the explicit web proxy?
A. host 192.168.0.2 and port 8080\\' B.host 10.0.0.50 and port 80\’
C. host 192.168.0.1 and port 80\\' D.host 10.0.0.50 and port 8080\’
Correct Answer: A
QUESTION # 9
Which three criteria can a FortiGate use to look for a matching firewall policy to process traffic? (Choose three.)
A. Source is defined as Internet Services in the firewall policy.
B. Destination is defined as Internet Services in the firewall policy.
C. Highest to lowest priority defined in the firewall policy.
D. Services defined in the firewall policy.
E. Lowest to the highest policy ID number.
Correct Answer: ABD
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD47435
QUESTION # 10
Refer to the exhibit.
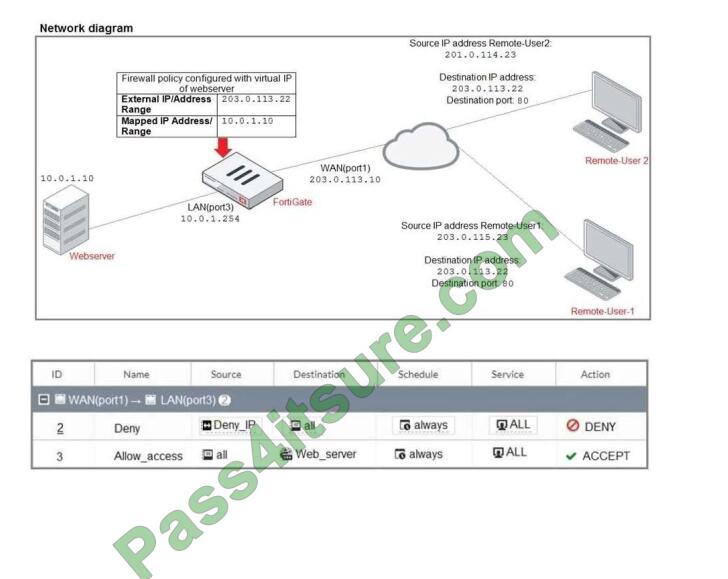
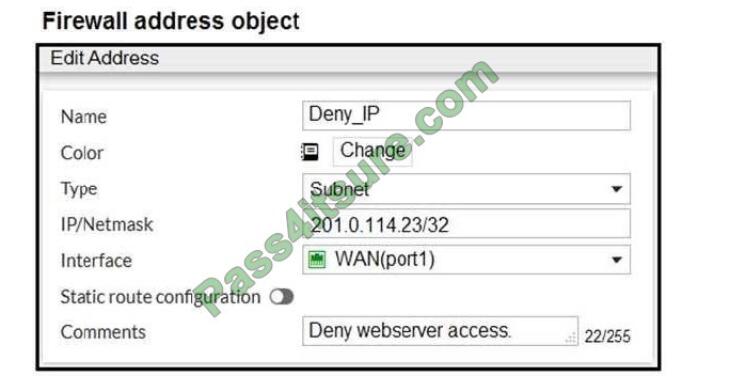
The exhibit contains a network diagram, firewall policies, and a firewall address object configuration. An
administrator created a Deny policy with default settings to deny Webserver access for Remote- user2.
Remote-user2 is still able to access Webserver.
Which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose
two.)
A. Disable match-VIP in the Deny policy.
B. Set the Destination address as Deny_IP in the Allow-access policy.
C. Enable match VIP in the Deny policy.
D. Set the Destination address as Web_server in the Deny policy.
Correct Answer: AB
QUESTION # 11
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
A. DNS
B. ping
C. UDP-echo
D. TWAMP
Correct Answer: AC
QUESTION # 12
In an explicit proxy setup, where is the authentication method and database configured?
A. Proxy Policy
B. Authentication Rule
C. Firewall Policy
D. Authentication scheme
Correct Answer: D
QUESTION # 13
What devices form the core of the security fabric?
A. Two FortiGate devices and one FortiManager device
B. One FortiGate device and one FortiManager device
C. Two FortiGate devices and one FortiAnalyzer device
D. One FortiGate device and one FortiAnalyzer device
Correct Answer: C
Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/425100/components
Download the NSE4_FGT-7.0 dumps (free) address https://drive.google.com/file/d/1q1QpJio3epd-Zbhe2rCE5UR9yLrn1Lh9/view?usp=sharing
More questions NSE4_FGT-7.0 exam on this website.