Most Effective Success Fortinet NSE4_FGT-6.4 Dumps Pdf ProblemMost Effective Success Fortinet NSE4_FGT-6.4 Dumps Pdf Problem

The most effective way to pass the Fortinet NSE4 NSE4_FGT-6.4 exam is to take the latest NSE4_FGT-6.4 dumps pdf 2022!
Why take the Fortinet NSE 4 – FortiOS 6.4 exam?
Passing the exam will give you high-paying jobs and the prospect of academic success.
Why is Fortinet NSE4_FGT-6.4 dumps pdf the most effective way to succeed in your exam?
NSE4_FGT-6.4 exams are considered to be one of the most difficult exams to prepare for, and it is difficult to pass without the right methods. NSE4_FGT-6.4 dumps pdf is the right way! It provides up-to-date and authentic NSE4_FGT-6.4 practice exam questions and answers that will help pass the exam.
Pass4itSure is one of the world’s leading brands and offers the best and relevant Fortinet NSE 4 – FortiOS 6.4 NSE4_FGT-6.4 practice exam materials for you to prepare. Latest NSE4_FGT-6.4 dumps pdf >>> https://www.pass4itsure.com/nse4_fgt-6-4.html (PDF +VCE)
Authentic Fortinet NSE 4 – FortiOS 6.4 NSE4_FGT-6.4 practice test
NSE4_FGT-6.4Q&As
QUESTION 1
Which three methods are used by the collector agent for AD polling? (Choose three.)
A. FortiGate polling
B. NetAPI
C. Novell API
D. WMI
E. WinSecLog
Correct Answer: BDE
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD47732
QUESTION 2
Which of the following statements correctly describes FortiGates route lookup behavior when searching for a suitable
gateway? (Choose two)
A. Lookup is done on the first packet from the session originator
B. Lookup is done on the last packet sent from the responder
C. Lookup is done on every packet, regardless of the direction
D. Lookup is done on the trust reply packet from the responder
Correct Answer: AD
QUESTION 3
Refer to the exhibit to view the application control profile.
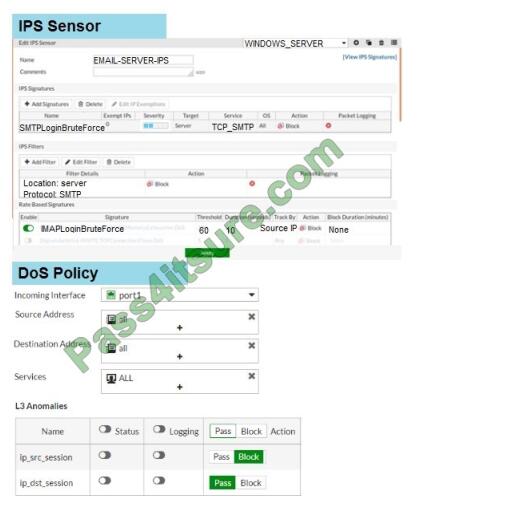
Users who use Apple FaceTime video conferences are unable to set up meetings. In this scenario, which statement is
true?
A. Apple FaceTime belongs to the custom monitored filter.
B. The category of Apple FaceTime is being monitored.
C. Apple FaceTime belongs to the custom blocked filter.
D. The category of Apple FaceTime is being blocked.
Correct Answer: A
QUESTION 4
View the exhibit.
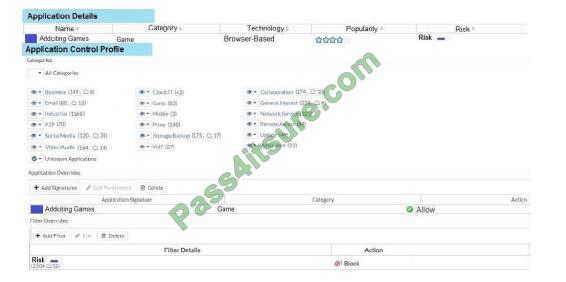
A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting Games). Based on this
configuration, which statement is true?
A. Addicting. Games are allowed based on the Application Overrides configuration.
B. Addicting. Games are blocked on the Filter Overrides configuration.
C. Addicting. Games can be allowed only if the Filter Overrides actions are set to Exempt.
D. Addicting. Games are allowed based on the Categories configuration.
Correct Answer: A
QUESTION 5
How does FortiGate act when using SSL VPN in web mode?
A. FortiGate acts as an FDS server.
B. FortiGate acts as an HTTP reverse proxy.
C. FortiGate acts as a DNS server.
D. FortiGate acts as a router.
Correct Answer: C
QUESTION 6
Refer to the exhibit.

Which contains a network diagram and routing table output.
The Student is unable to access Webserver.
What is the cause of the problem and what is the solution for the problem?
A. The first packet sent from the Student failed the RPF check. This issue can be resolved by adding a static route to
10.0.4.0/24 through wan1.
B. The first reply packet for Students failed the RPF check. This issue can be resolved by adding a static route to
10.0.4.0/24 through wan1.
C. The first reply packet for Students failed the RPF check. This issue can be resolved by adding a static route to
203.0.114.24/32 through port3.
D. The first packet sent from the Student failed the RPF check. This issue can be resolved by adding a static route to
203.0.114.24/32 through port3.
Correct Answer: C
QUESTION 7
Which two statements about antivirus scanning mode are true? (Choose two.)
A. In proxy-based inspection mode, files bigger than the buffer size are scanned.
B. In flow-based inspection mode. FortiGate buffers the file, but also simultaneously transmits it to the client.
C. In proxy-based inspection mode, antivirus scanning buffers the whole file for scanning, before sending it to the client.
D. In flow-based inspection mode, files bigger than the buffer size is scanned.
Correct Answer: CD
QUESTION 8
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
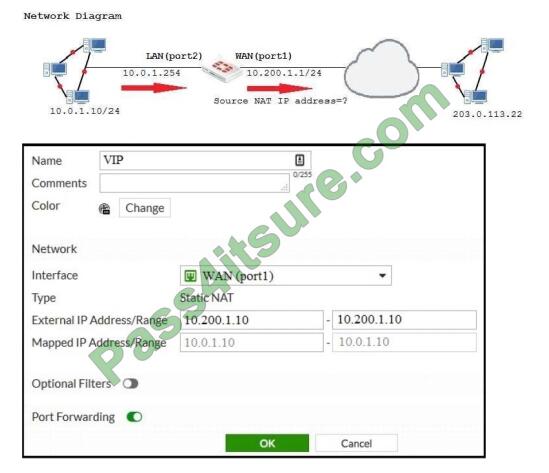
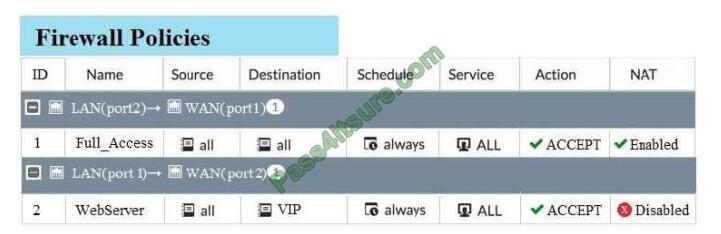
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address
10.0.1.254/24. The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is
configured with a VIP as the destination address. Which IP address will be used to source NAT the Internet traffic
coming from a workstation with the IP address 10.0.1.10/24?
A. 10.200.1.10
B. Any available IP address in the WAN (port1) subnet 10.200.1.0/24
C. 10.200.1.1
D. 10.0.1.254
Correct Answer: B
QUESTION 9
View the exhibit.
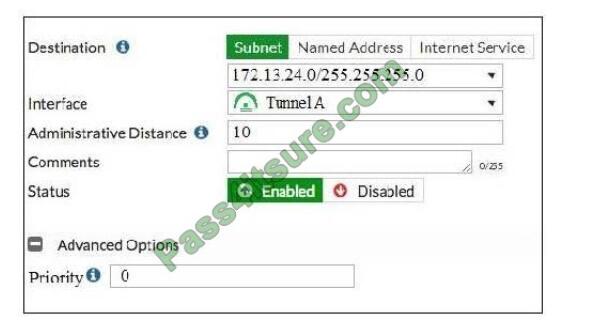
Which of the following statements are correct? (Choose two.)
A. This setup requires at least two firewall policies with the action set to IPsec.
B. Dead peer detection must be disabled to support this type of IPsec setup.
C. The TunnelB route is the primary route for reaching the remote site. The tunnel route is used only if the Tunnell
VPN is down.
D. This is a redundant IPsec setup.
Correct Answer: CD
QUESTION 10
What devices form the core of the security fabric?
A. Two FortiGate devices and one FortiManager device
B. One FortiGate device and one FortiManager device
C. Two FortiGate devices and one FortiAnalyzer device
D. One FortiGate device and one FortiAnalyzer device
Correct Answer: C
Reference: https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/425100/components
QUESTION 11
Refer to the exhibit.
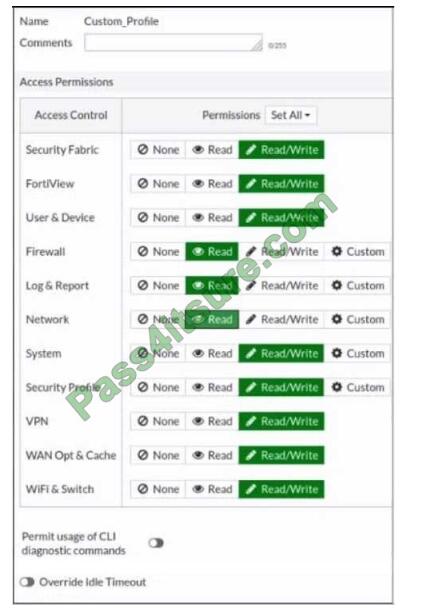
Based on the administrator profile settings, what permissions must the administrator set to run the diagnosed firewall
auth list CLI command on FortiGate?
A. Custom permission for Network
B. Read/Write permission for Log and Report
C. CLI diagnostics commands permission
D. Read/Write permission for Firewall
Correct Answer: A
QUESTION 12
Which two inspection modes can you use to configure a firewall policy on a profile-based next-generation firewall
(NGFW)? (Choose two.)
A. Proxy-based inspection
B. Certificate inspection
C. Flow-based inspection
D. Full Content inspection
Correct Answer: AC
Also, free Fortinet NSE 4 – FortiOS 6.4 dumps pdf download
google drive: https://drive.google.com/file/d/1GP6K6KQYBquiGnuwExJbMiC83VH2un4w/view?usp=sharing
At Pass4itSure, you will receive a real NSE4_FGT-6.4 dumps pdf which contains questions similar to a real exam and provides the correct answer at the end to pass your NSE4_FGT-6.4 certification exam. Related links >>> https://www.pass4itsure.com/nse4_fgt-6-4.html (Total Questions163).
With these, as long as you practice diligently, you can successfully obtain NSE4 certification.